Monitor every exposed asset before adversaries do
ExternalScan helps security teams map, monitor, and secure their Internet-facing infrastructure with continuous discovery, contextual risk scoring, and analyst-backed validation.
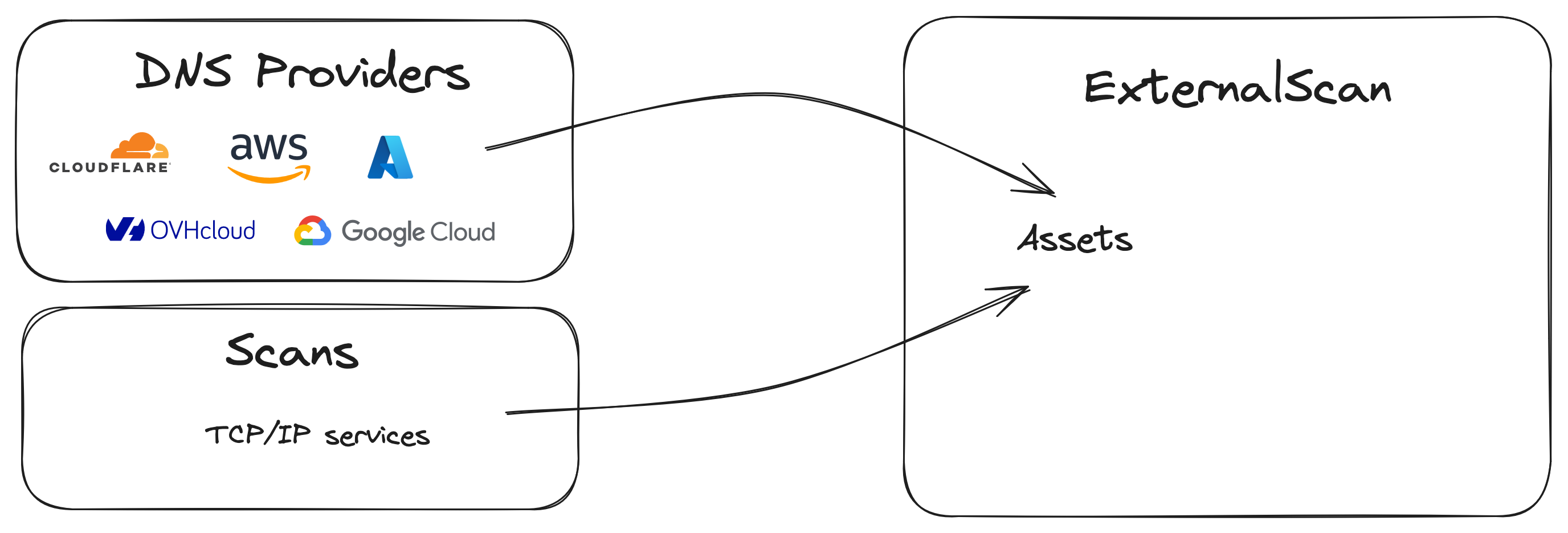
- Continuous asset discovery across DNS, cloud, and shadow IT.
- Prioritized vulnerabilities with contextual risk scoring.
- Human analysts validate every high-impact finding.
- Assets monitored daily
- 120k+
- Connectors available
- 45+
- Average detection time
- <15 min
Across DNS, cloud, and Internet-facing services.
DNS, cloud, ticketing, and collaboration ecosystems.
From exposure to alert across monitored assets.
Capabilities
An EASM suite built for modern security teams
Cover the entire lifecycle from discovery to remediation with a unified control plane that keeps every stakeholder aligned.
Asset Discovery
Automatically index every domain, IP, certificate, and service exposed on the Internet.
- DNS zone ingestion, SSL/TLS analysis, and passive DNS enrichment.
- Cloud-native discovery for AWS, Azure, GCP, and SaaS.
Risk Prioritization
Understand which exposures represent real risk thanks to contextual scoring enriched with business impact.
- CVSS, exploitability, and business sensitivity rolled into one score.
- Analyst notes and remediation paths surfaced for every critical issue.
Continuous Monitoring
Keep watch on changes in your perimeter with differential scanning and proactive alerting.
- Daily baseline scans with drift detection.
- Instant notifications when new services or vulnerabilities appear.
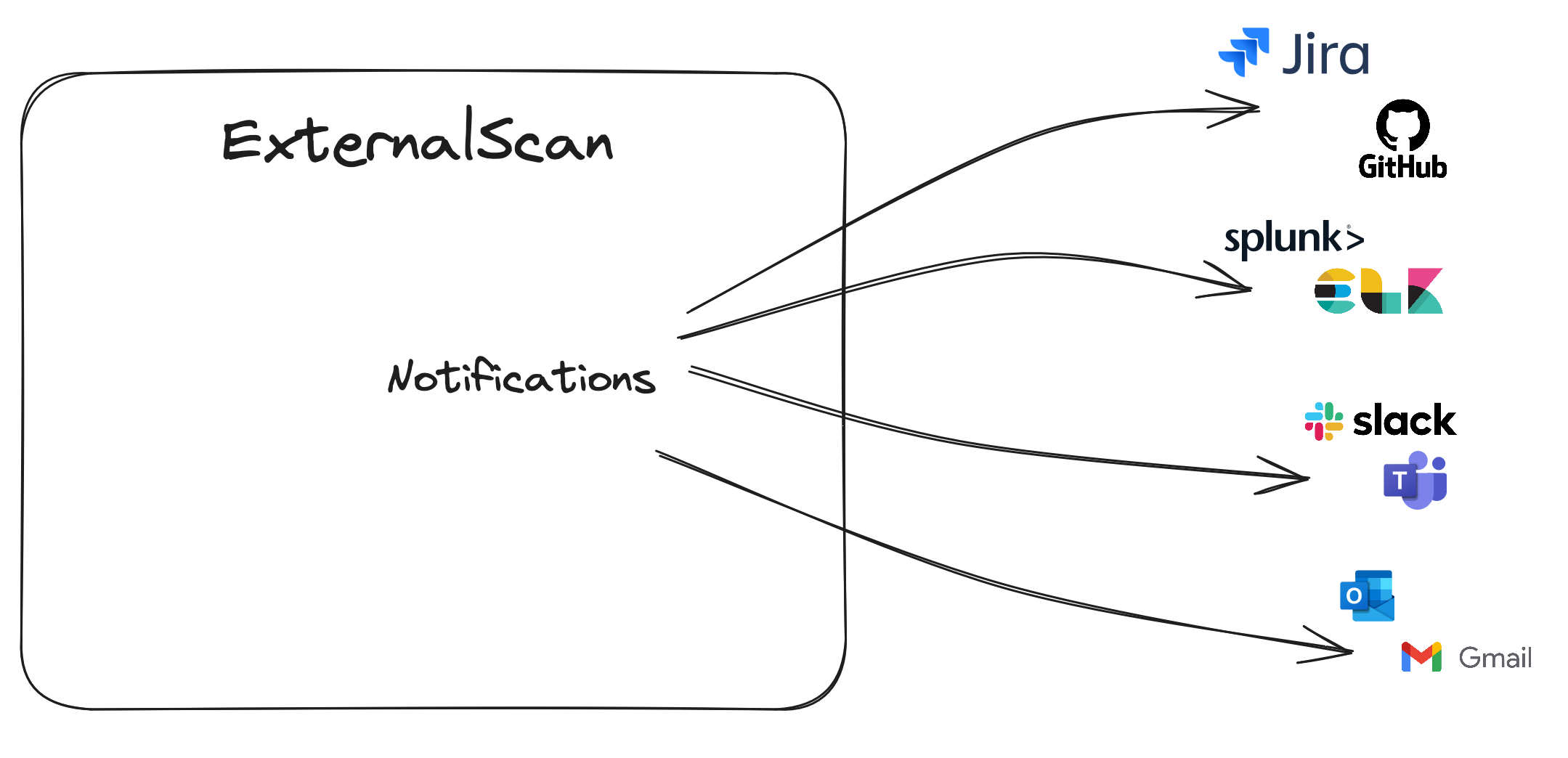
Collaboration & Integrations
Bring ExternalScan insights into the tools your teams already use.
- Push tickets automatically to ServiceNow, Jira, and Trello.
- Bidirectional messaging with Slack, Teams, and email.
Executive Reporting
Share progress and trends with leadership using real-time dashboards and scheduled digests.
- Customizable executive dashboards and PDF exports.
- Program health metrics ready for board and regulator reviews.
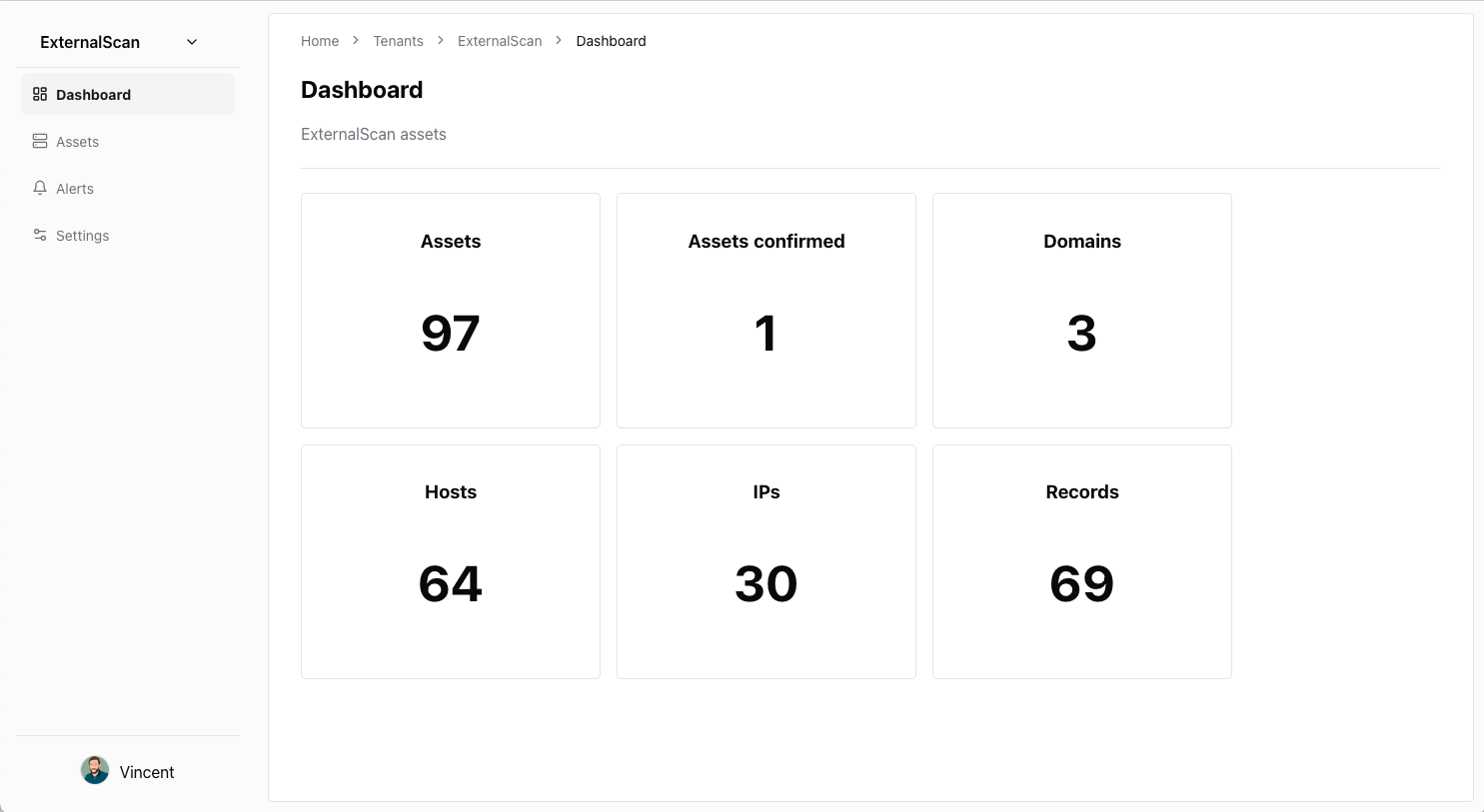
Discover
Full-spectrum external asset inventory
- Agentless discovery across DNS, cloud accounts, and shadow IT.
- Automatic service fingerprinting with port, protocol, and technology detection.
- Real-time tagging to group assets by business unit or sensitivity.
Inventory updates stream into the platform in near real-time so teams always see the latest exposure.
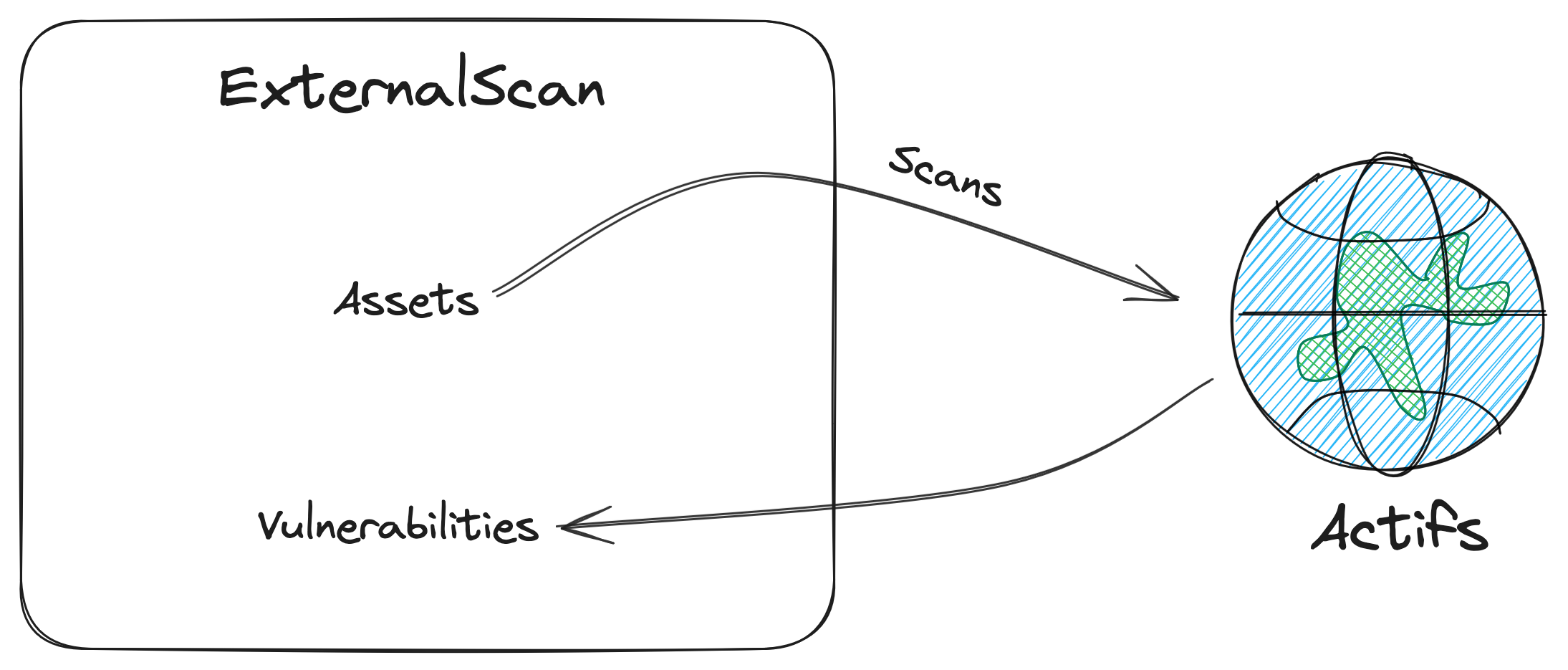
Prioritize
Risk scoring backed by analyst validation
- Hybrid automated and manual verification for high-impact exposures.
- Context-aware scoring aligned with CVSS, EPSS, and exploit data.
- Root-cause insights and recommended next actions for every issue.
Security analysts validate critical findings to cut through alert fatigue.
Respond
Automated workflows that close the loop
- Native integrations with Slack, Teams, Jira, ServiceNow, and PagerDuty.
- Change timelines that capture acknowledgement, fix, and retest events.
- Role-based access controls with full audit trails.
Orchestrate remediation with automated playbooks or export findings to your SOAR platform.
Operating model
How ExternalScan keeps your perimeter safe
Adopt a repeatable playbook that removes blind spots, accelerates remediation, and proves control to stakeholders.
Discover everything automatically
Map the perimeter
We continuously ingest DNS, cloud, certificate, and web intelligence to build a unified inventory of Internet-facing assets.
- Agentless discovery refreshes whenever your infrastructure changes.
- Shadow IT is surfaced through passive and active reconnaissance.
Validate and prioritize risk
Know what matters
Automated checks and security analysts validate exposures, enrich them with business context, and rank them by impact.
- Exploit intelligence and severity scoring combined in one signal.
- Business tags highlight accountable owners instantly.
Orchestrate remediation
Act with confidence
Route findings to the right teams, track progress, and confirm resolution with retests and continuous monitoring.
- Automated ticketing and messaging integrations.
- Retest windows verify fixes and guard against regressions.
Use cases
Flexible for every security mission
Security, risk, and product teams use ExternalScan to illuminate their attack surface and respond faster.
Attack surface assessment
Know what is exposed
Produce a complete inventory of web, cloud, and network assets with severity-ranked exposures ready for compliance or M&A reviews.
ExposureContinuous vulnerability monitoring
Stay ahead of attackers
Detect configuration drift, leaked services, and high-risk vulnerabilities minutes after they appear on the Internet.
MonitoringExecutive reporting & compliance
Prove control
Share digestible reports with leadership and regulators, showing trends, ownership, and remediation progress over time.
ReportingNeed answers?
Frequently asked questions
Everything you need to know before rolling out ExternalScan across your organization.
Ready to see your entire external attack surface?
Launch ExternalScan now or schedule a guided tour with our security team to explore continuous discovery, validation, and remediation workflows tailored to you.
Talk to an EASM expert